|
Hacker threat to city systems
By STEPHEN BIRCH
Daily Telegraph
30 January 2002
BIG companies run the risk of losing millions of dollars through hackers breaking into their wireless computer networks and gaining access to sensitive information, a computer expert warned yesterday.
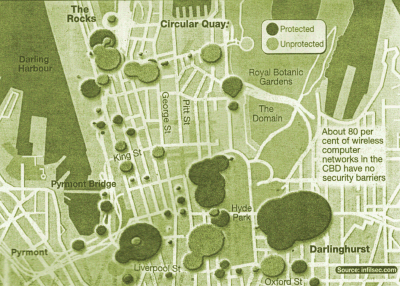
Matt Barrie, chief technology officer of computer security firm Infilsec, said a study of 600 corporate wireless computer networks in the Sydney CBD found 80 per cent had no security barriers.
This meant anyone with a laptop computer and a wireless card could hack into the wireless networks - potentially gaining access to information about financial records or research.
Mr Barrie said yesterday many people who used the wireless computers for business were not too concerned about going through security protocols.
"It's good technology - the problem is people have adopted it en masse without thinking too much about security," he said.
"When people buy new things, they like to have it work first go. They generally like to have it so they pull it out of the box, they turn it on, and it works.
"Because the technology is so easy to use, the people who benefit the most from it tend to be the least technical.
"If the computer is to be used by a number of different people, it can be a hassle to have to go through security protocols."
People often did not change the computer from its default security configuration, making it easier to break into.
"You don't have to be a hacker to break in," he said.
"On a live network, each of the access points puts out a beacon, saying 'Hi, I'm here'. Most of the networks that are out there will allow you easy access."
Wireless technology uses radio signals to connect computers.
Users put information on wireless cards which they plug into the computer, allowing information to be moved from computer to computer.
Infilsec's survey found 15 per cent of the unsecured networks used their organisation's name as the identifying mark.
About 28 per cent of companies used the default identifier provided by the manufacturer of the computer technology.
Mr Barrie said the standard security system which came with wireless technology, known as Wired Equivalent Privacy (WEP), was easily circumvented.
"By the time they put the computers out with WEP included, they realised it [the security system] was broken," he said.
Mr Barrie said people needed to treat their wireless technology security more seriously.
"Some of the big companies are aware of it," he said.
____
Welcome to our Techical Site. If you are interested in an overview, then visit our
Marketing Site
Copyright © 1994-2005
Radioactive Networks ,
darryl@radio-active.net.au
This page was last updated 2005-08-31 15:00:08
This page was last compiled 2005-11-15 19:02:59
Question or Comment? Click
here
|

